
Licensing of software used in companies. It's not easy, but we can handle it.


![]() Ensuring the operation of a computer network
Ensuring the operation of a computer network
We will take care of the users and hardware of your computer network under pre-agreed conditions
![]() Helpdesk and support
Helpdesk and support
![]() Consultation for development of IT infrastructure
Consultation for development of IT infrastructure
Consulting services related to strategic planning and development plans in the field of information and communication infrastructure
![]() Service and prophylaxis
Service and prophylaxis
We also perform routine repairs of corporate hardware directly related to the operation of the company's ICT infrastructure
![]() Instalation of hardware and software
Instalation of hardware and software
![]() Servers and active items of PC networks
Servers and active items of PC networks
We supply more complex computer systems, especially physical servers and active elements of computer networks and selected application solutions
![]() Consuling support to comercial IT departments
Consuling support to comercial IT departments
We provide consulting support to IT staff in solving problems associated with the operation of corporate computer networks and IT infrastructure
![]() Educate Me! Traininng and courses of computer literacy
Educate Me! Traininng and courses of computer literacy ![]()
We increase computer literacy and qualification of employees of private companies and organizations

The computer security company
We are a company providing consulting, implementation, service, sales and technical support of ICT infrastructure in companies and organizations. "Diestra" - in Spanish right hand. Diestra comprende, or if you will, Diestra understands and gives its customers the right hand in solving computer problems and the functioning of corporate networks. Shake your right with IT specialists and salespeople from a stable company operating in their field since 2007. Our goal is to ensure the proper and secure operation of your corporate IT. You will have both hands free to develop and manage your company.
We educate users not only in office software
Computer literacy is a set of knowledges, abilities and skills, wich are focused on operating and using computer in personal both working life. Computer literacy skilled person can handle Personal Computer with common computer software, including it's hardware and use computer network (primarily internet). Get computer skills, especially in most known office applications, like Microsoft Word, Excel and Outlook are. Learn to use them effectively. Also you can send to training your colleagues or employers and rise their computer abilities and thus productivity. Our lecturers from Educate Me! division will help you very glad with choice of the most suitable course, or with the compilling the curriculum, what will meet your requirements and your options.

Licensing of software used in companies. It's not easy, but we can handle it.


Antivirus on mobile devices. Yes or No?
Our specialists are speaking about spearphising, social engeneering squared at least. Something like "new type of upgraded phising."



Technology base of device
Integrated, compact and comfortable measuring system
The device is controlled by a industrial CPU
Definition : IoT category
Resistance according to standard: IP68
Diestra® MONITORING™
check / inspect the following parameters:
• position of the mechanical component - open / closed status detection
• status of the mechanical component - communicates / doesn't communicate
• pressure / vacuum level in the monitored technology
• GPS position monitoring
• current status of monitoring batteries
• ambient temperatur
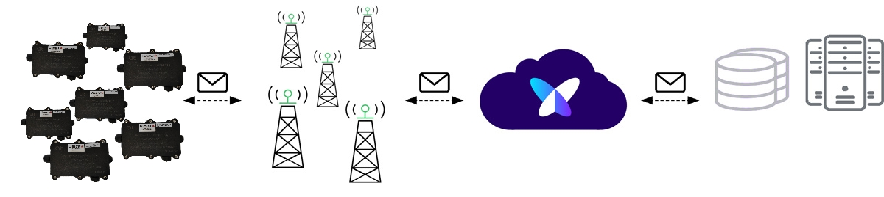
Type of data communication
• sending change states of sensory measurements: component 1 / component 2
• sending data at regular intervals to the database via IoT network SigFox
• sending data based on the sent request towards Monitoring (optional)
About SIGFOX
• meets the requirements for mass applications
• allows operation with a very long battery life
• secure communication network architecture, interference immunity
• stable uplinl / downlink operation
• ultra-band radio modulation
• the transmission is not synchronized between the device and the network
• high emphasis on the security of transmitted data
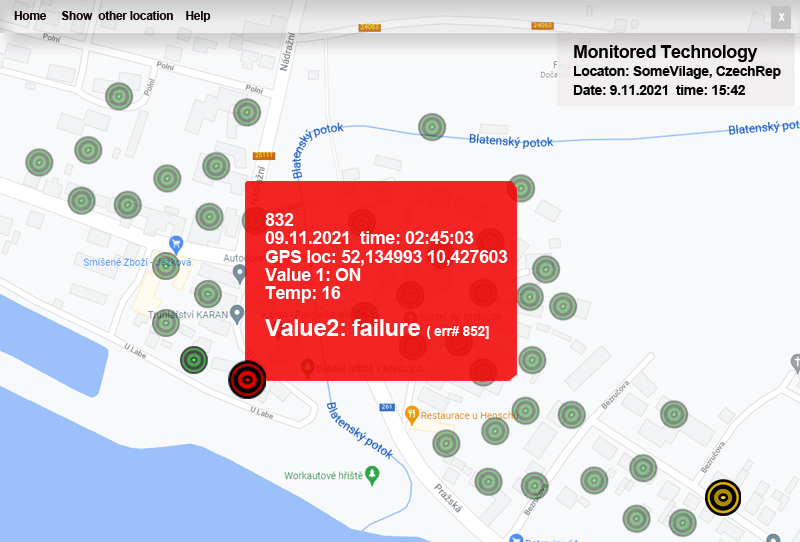
Format of the acquired data
(options according to the requirements of the end user):
• basic line display of data distributed for use in the client's own surveillance system
• tabular display of monitoring status and subsequently data (basic data view)
• display of monitoring status and subsequently data on a map base based on the provided GPS position
Guarantee
• Guaranteed battery life per one charge: 24 months
• Estimated battery life per one charge: 48 months (and more)
• Warranty: 24 months
How it works?
Diestra® Monitoring™ > Helpdesk
Radio Configuration 1: 868-878.6 MHz with EIRP* = 16 dBm.
Vizualization
Diestra® Monitoring™ Helpdesk
interested? ask for more here






